This part of the website is
Under Construction
In the meantime, you can browse the rest of the site or get in touch with us through our other channels!
NIS2 is a directive from the European Commission that outlines expectations for a high common level of cybersecurity for European organizations in critical sectors. The European Parliament approved the NIS2 Directive on 10 November 2022, with an effective date of 17 October 2024.
How to Use Policy as Code for Easier NIS2 Compliance at Enterprise Scale
How to Use Policy as Code to Stay NIS2 Compliant
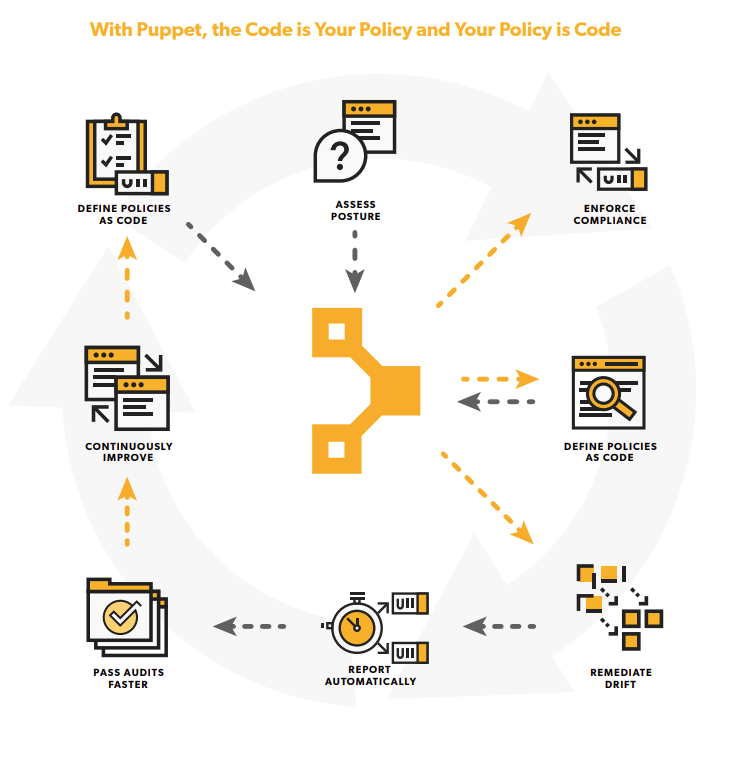
Policy as code (PaC) is a three-step method: Defining your IT security policies, writing infrastructure configurations as code to align your critical systems to those policies, and using automation to redeploy that infrastructure code automatically whenever something falls out of compliance.
As a concept, PaC lets you declare your infrastructure state as code and automatically fix deviations. Especially when it comes to the high expectations and harsh penalties of NIS2, PaC is a key component of maintaining security and compliance in the enterprise.
How to Use Policy as Code to Stay NIS2 Compliant?
MAPPING POLICY AS CODE CAPABILITIES TO KEY NIS2 REQUIREMENTS
Automatically enforcing system hardening measures at scale
Key NIS2 requirements covered:
- Risk assessments and security policies
- Procuring, developing, and operating secure systems
- Policies for data access by employees
- Multi-factor authentication
- Evaluating security measure effectiveness
Generating reports and documentation automatically or on demand
Key NIS2 requirements covered:
- Risk assessments and security policies
- Procuring, developing, and operating secure systems
- A detailed response plan (reporting/notification)
Enforcing security hardened, compliant configurations on new and existing system components
Key NIS2 requirements covered:
- Risk assessments and security policies
- Procuring, developing, and operating secure systems
- Policies for data access by employees
- Multi-factor authentication
- Evaluating security measure effectiveness
Using Puppet for
Security Hardening & Continuous Compliance
HERE’S HOW IT WORKS:
- Puppet infrastructure as code (IaC) defines your desired compliance state, including all your internal and external compliance policies as well as custom exceptions.
- Puppet continually scans your managed servers to assess your compliance status throughout cloud and on-premises environments.
Agent-Based vs. Agentless Tools for NIS2 Compliance
Puppet vs. Ansible: Understanding the Difference
Because agentless automation tools like Ansible rely on network connectivity, they can’t ensure the round-the-clock desired state enforcement needed for continuous compliance.
Executing automation tasks locally rather than remotely also gives you server-level control and reporting capabilities, local security permissions, and the ability to handle more complex tasks by leveraging local CPU and memory resources.



